Welcome to Intelligent Software Crafted to Support Growth, Change, and Opportunity
Seamlessly integrate A/B/n testing into your digital products with support for multiple variants, statistical analysis, and real-time user segmentation to drive evidence-based decisions.
₦32,371.82
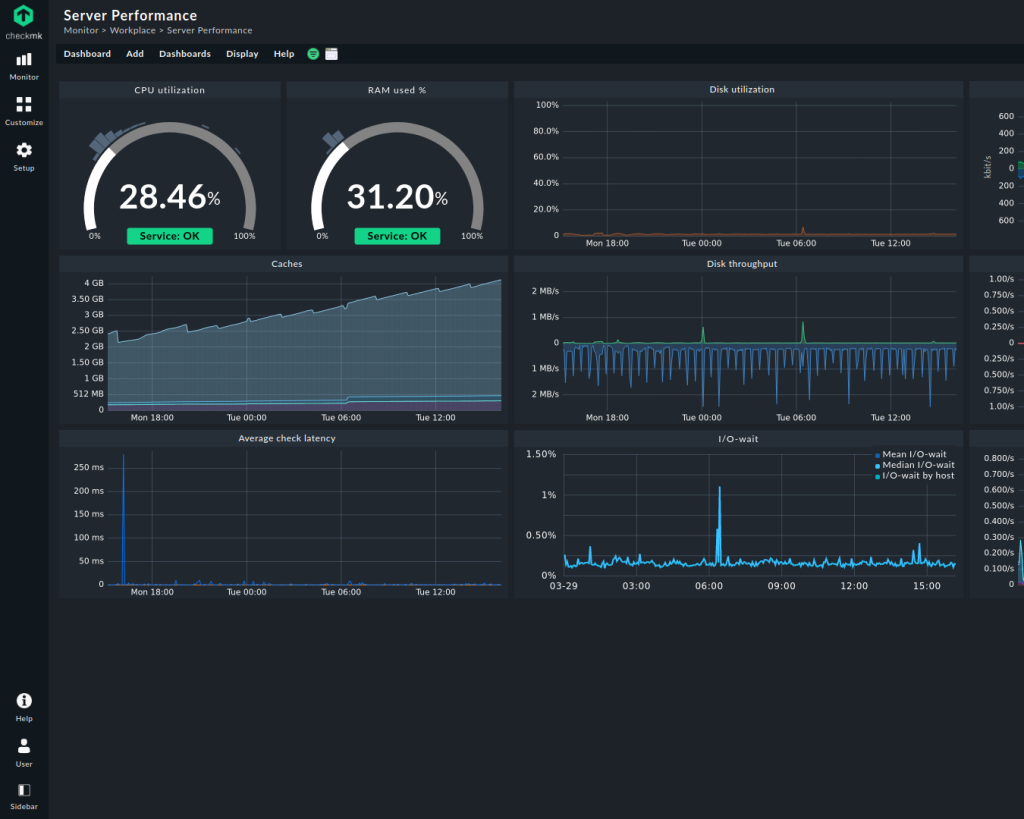
Track and visualize your machine learning model’s real-time performance with dashboards that monitor accuracy, latency, and prediction quality across environments.
₦73,481.56

Detect concept and data drift in ML models using statistical analysis and real-time alerts, ensuring reliability and trustworthiness of predictions over time.
₦74,263.91

Automate the model building process with AutoML pipelines that handle data cleaning, feature selection, model selection, and hyperparameter tuning—at scale.
₦25,641.29
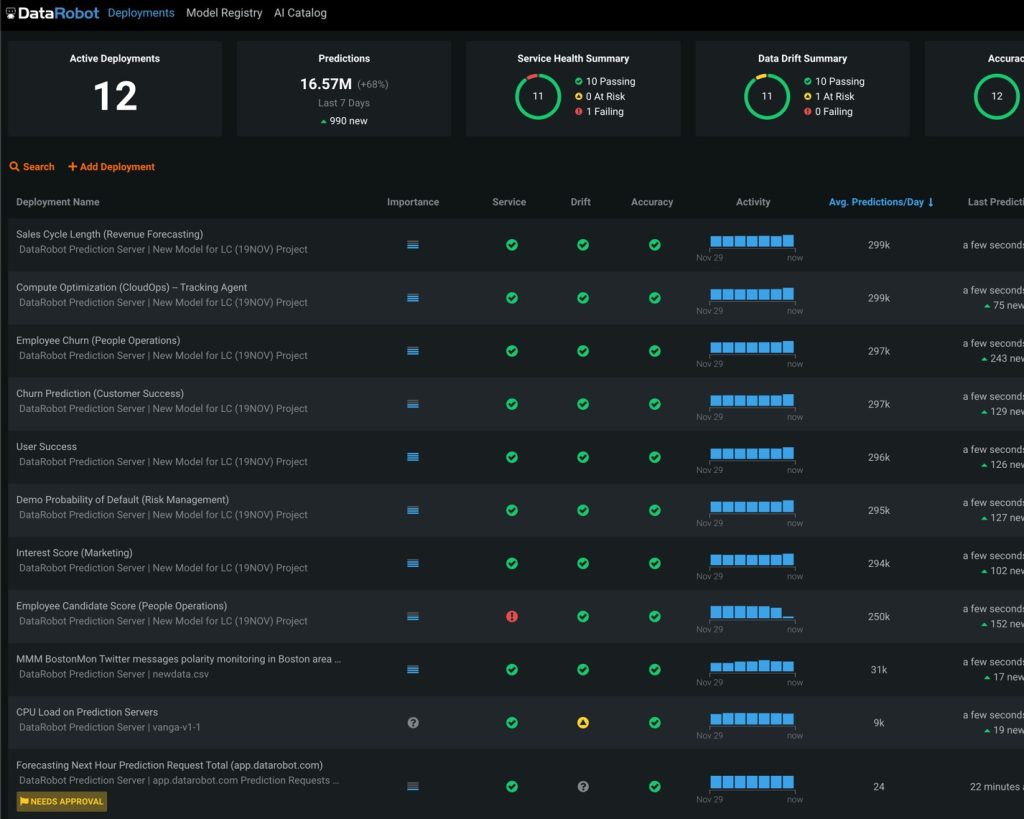
Gain complete control over model lifecycles with a dashboard that tracks versions, metadata, deployments, access logs, and audit trails—supporting secure and compliant ML ops.
₦69,287.31

Automate the detection of internal threats using behavior analytics, anomaly detection, and contextual access monitoring to protect sensitive systems from within.
₦51,365.73

Run realistic phishing campaigns and score employee risk levels based on responses, enabling personalized training and organization-wide security posture improvement.
₦78,123.47
Deploy deceptive environments such as honeypots, breadcrumbs, and traps to lure and detect malicious actors before they reach real assets.
₦44,361.85

Continuously monitor dark web sources for leaked employee or customer credentials and get real-time alerts with actionable remediation steps.
₦55,261.84

Build a centralized platform to ingest, parse, normalize, and enrich threat intelligence feeds from multiple sources for faster detection and response.
₦95,074.52
Dynamically adapt web or app interfaces in real-time based on user behavior, intent, or interaction sequence to improve engagement and reduce drop-offs.
₦51,364.62

Influence user behavior with subtle, ethical nudges like timers, color cues, microcopy, and progress indicators to increase conversions without manipulation.
₦74,976.26

Integrate UI components that meet WCAG and ADA standards with built-in keyboard navigation, ARIA labels, and responsive design for inclusive user experience.
₦48,861.37
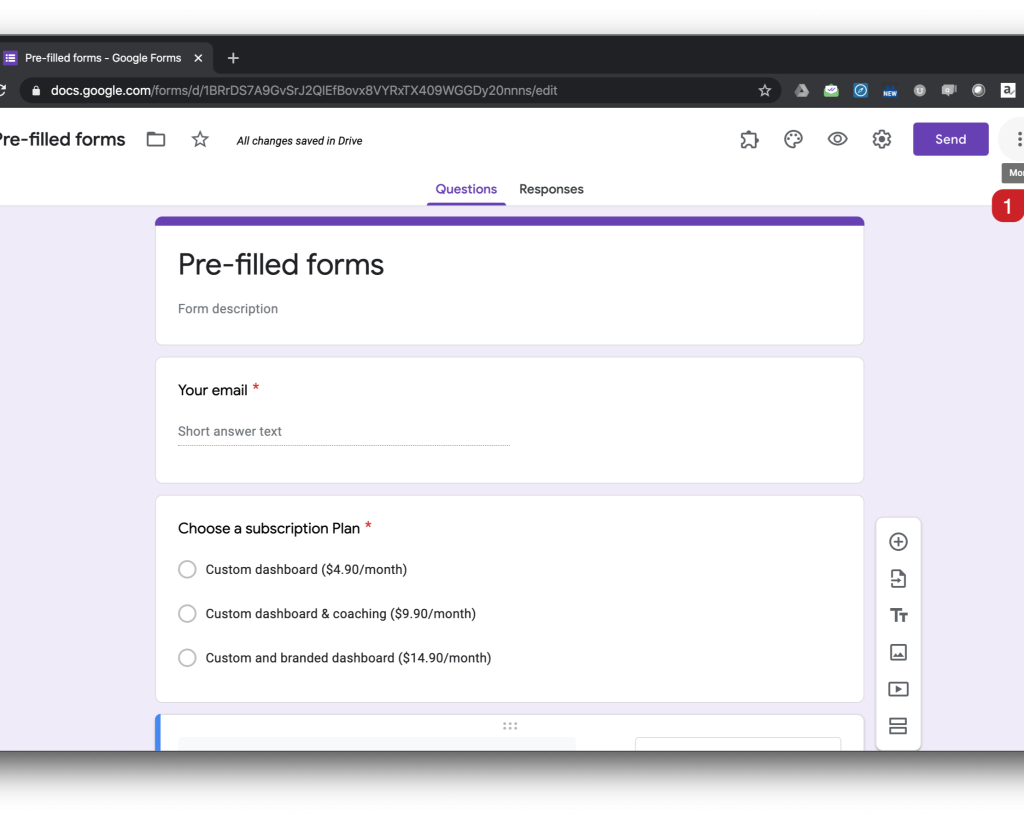
Auto-fill forms intelligently using session history, device fingerprinting, and permissioned user data to streamline onboarding, checkout, or lead capture flows.
₦62,108.73

Architect systems that use Command Query Responsibility Segregation (CQRS) with event sourcing to ensure immutable data logs, scalable reads/writes, and full audit trails.
₦40,264.53
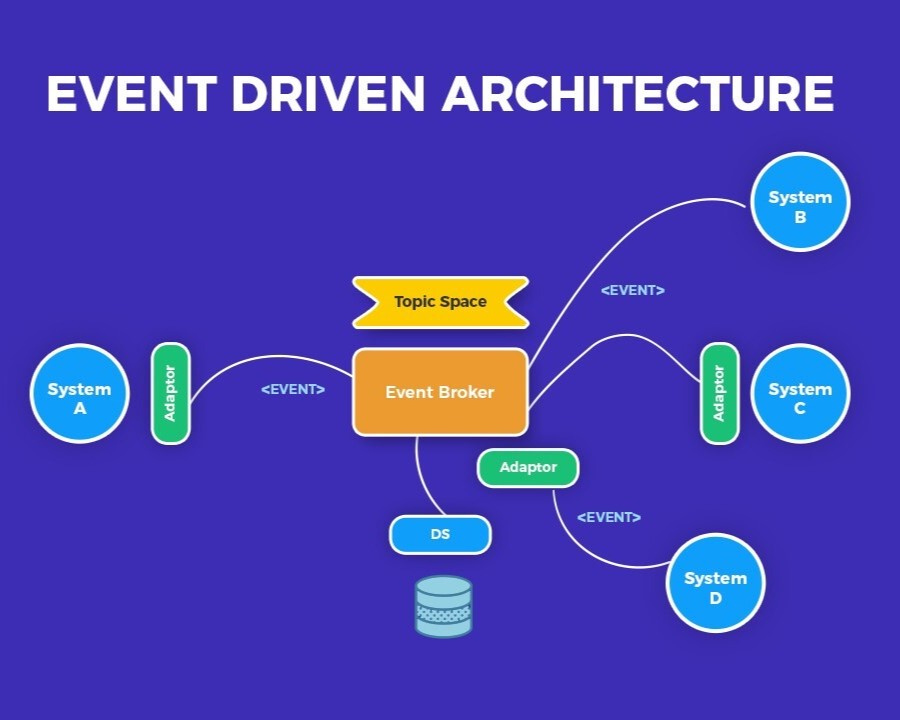
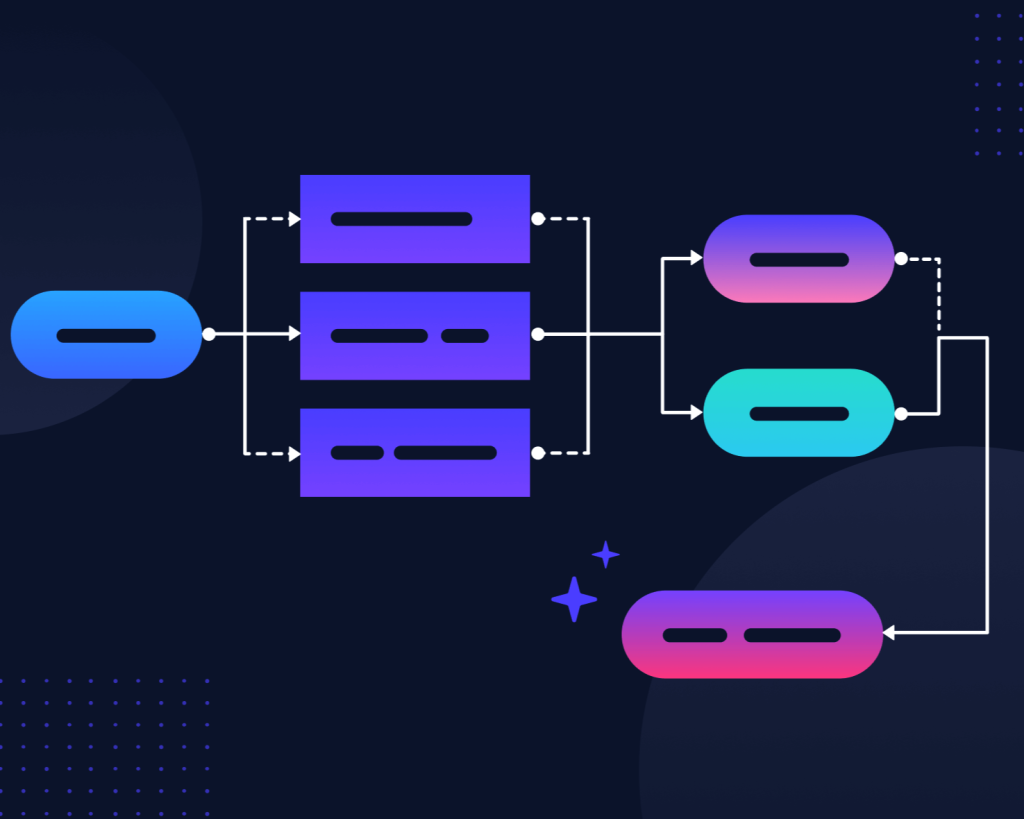
Design systems based on decoupled event producers and consumers using message queues, event buses, and reactive workflows for scalable and loosely coupled systems.
₦53,772.81
Visualize and analyze user paths using AI-enhanced heatmaps, funnel flows, and scroll-depth mapping to uncover friction points and improve UX design.
₦74,701.94

Implement service mesh layers for secure, observable, and manageable communication between microservices with features like mTLS, retries, and circuit breakers.
₦21,457.92
Design globally distributed architectures with real-time failover, DNS routing, and data replication to ensure high availability and zero service disruption across regions.
₦55,176.38

Plan and execute seamless system migrations—database, codebase, or infrastructure—without impacting users, using feature toggles, shadow deployments, and phased rollouts.
₦68,135.49

We offer analytical tools to assess engagement, satisfaction, communication flow, and culture alignment in remote teams, delivering insights for strategic HR improvements.
₦74,263.91
Copyright © 2025 Konneckt Vastmart Business Limited. All rights reserved